overleaf template galleryCommunity articles — Recent
Papers, presentations, reports and more, written in LaTeX and published by our community.
Algebra Linear

Reporte de inventario de evidencias

The rise of IoT interconnected objects will lead to an explosion in the volume of data that is collected, transmitted and processed. This explosion in volume will require novel methods for this transmission and processing.Power consumption and performance is one of the main design constraint for these systems. If current trends continue, future petaflop systems will require 100 megawatts of power. To address this problem the trend is towards the autonomous and responsible behavior of resources This demo shows how a network of ultra-low-voltage microprocessors platforms (Intel R AtomTM Processor E3815-Minnow-Max) can process their own data (running real HPC workloads) without the need of an external HPC system. This paper shows the impact of using a custom OS for x86 architecture in a embedded distributed system.

My Curriculum Vitae (English Version)

I have shown here how to derive the summation of a convergent Arithmetic series and get two results as answers
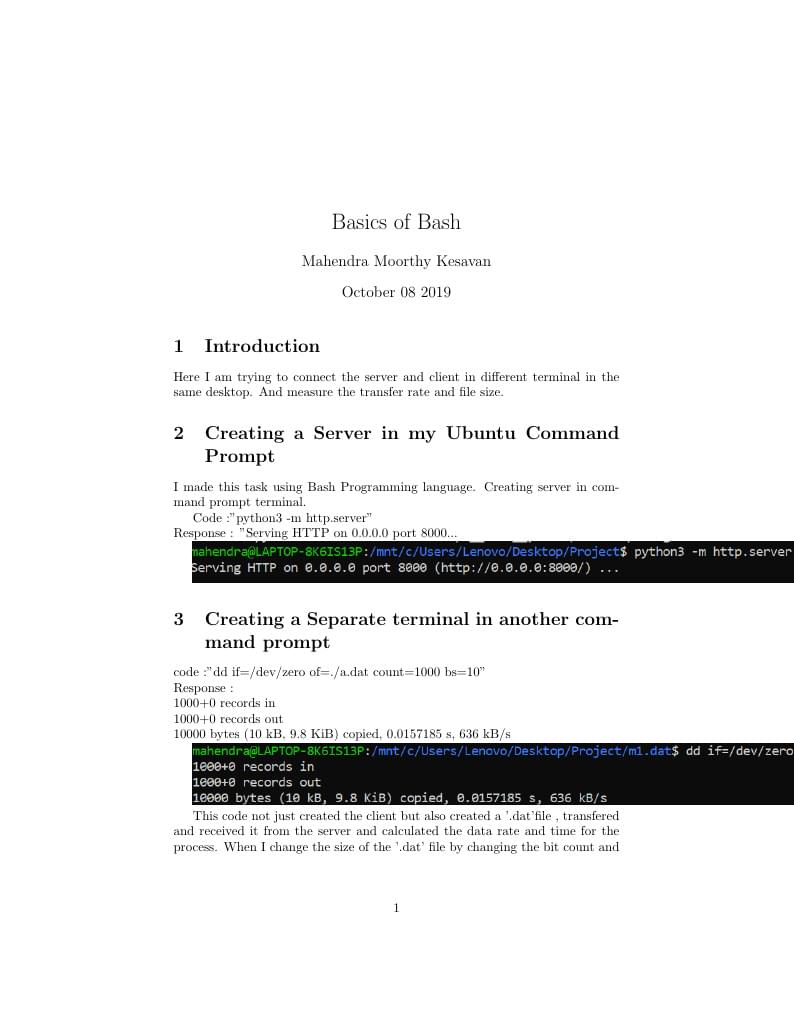
How to create client and server

Workshop and examples for getting started with LaTeX, Tufts 2016 CSLOL

Power consumption is a troublesome design constraint for HPC systems. If current trends continue, future petaflop systems will require 100 megawatts of power to maintain high-performance. To address this problem the power and energy characteristics of high performance systems must be characterised. The main idea of this project is to design a methodology for the optimal selection (minimal number of systems that maximise performance and minimise energy consumption) of a network topology for high performance applications using ultra-low-voltage microprocessors platforms (Intel® AtomTM Processor E3825 - Minnowboard).
\begin
Discover why over 25 million people worldwide trust Overleaf with their work.
