LaTeX templates and examples — Math
Recent

This template for submissions to the Journal of Statistical Software (JSS) was downloaded from the journal's website. There are templates for articles, code snippets, book reviews and software reviews. To use these for your own submission, open this template, and set the appropriate file to be your main file by right-clicking on them in the file list: article.tex codesnippet.tex bookreview.tex softwarereview.tex See README.txt and jss.pdf within this template for further information on how to use the template for your own submission.

ALSO AT https://www.overleaf.com/2407528pjqwrc

تمارين حول المتتاليات العددية
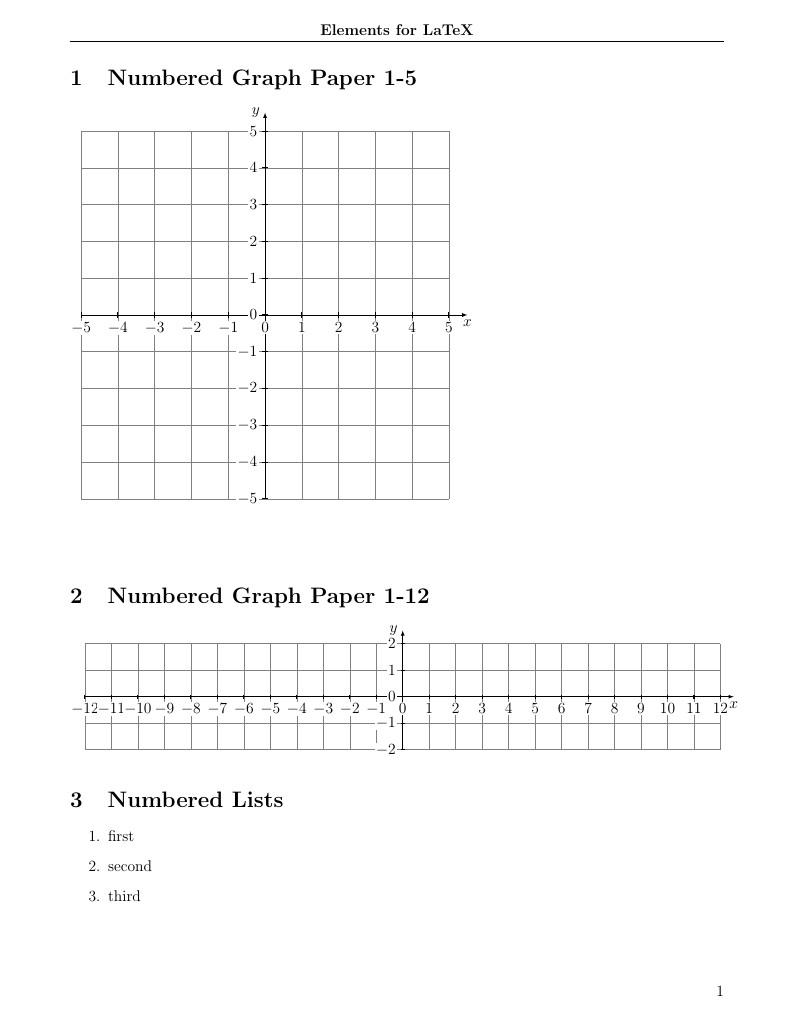
Just a collection of the code I've found and use regularly in projects. Includes crazy shapes, graph paper, margin changes and alignment of equations.
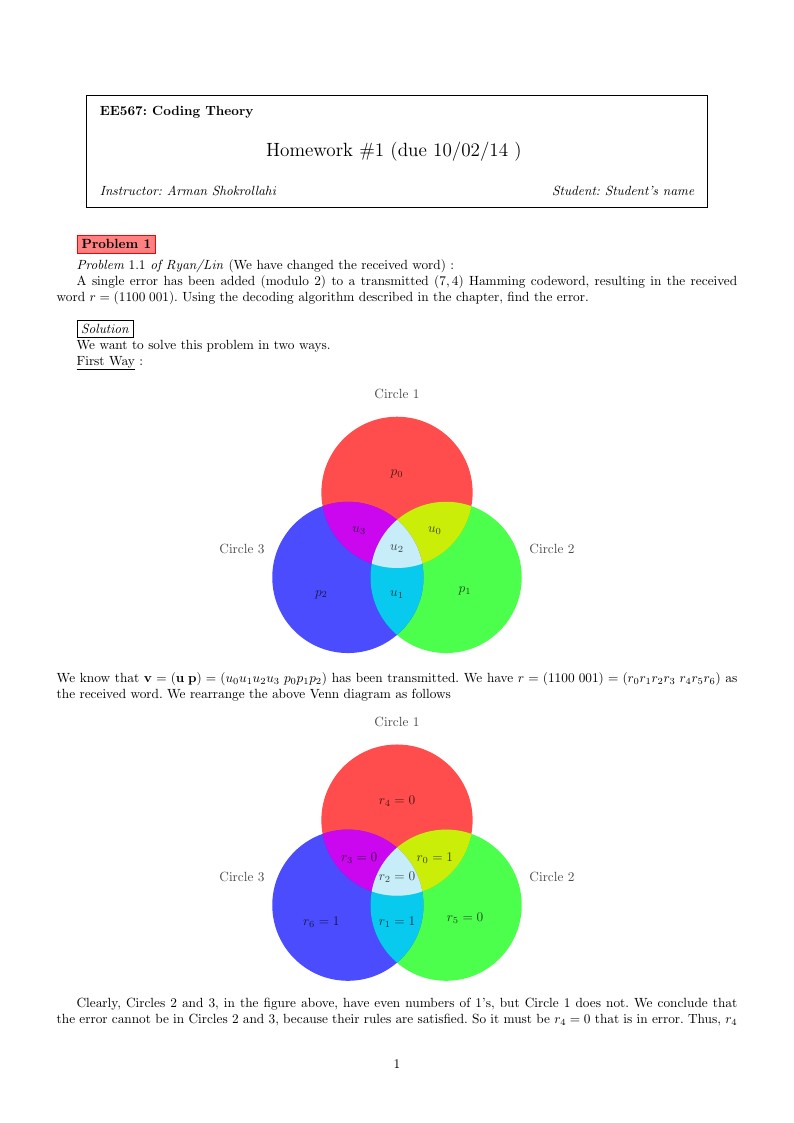
This is a LaTeX homework template I used for my coding theory course, ornamented with supplementary packages, such as Tikz. (The Venn diagram is created by me as well.)
\begin
Discover why over 25 million people worldwide trust Overleaf with their work.