Community articles — Two-column
Recent

Created using the Deedy - One Page Two Column Resume from LaTeX Template, Version 1.1 (30/4/2014). Original author: Debarghya Das (http://debarghyadas.com) Original repository: https://github.com/deedydas/Deedy-Resume

Lista de exercício com gabarito

Gene regulatory networks have an important role to study the behaviour of genes. By analysing these Gene Regulatory Networks we can get the detailed information i.e. the occurrence of diseases by changing behaviour of GRNs. Many different approaches are used (i.e. qualitative modelling and hybrid modelling) and various tools (i.e. GenoTech, GINsim) have been developed to model and simulate gene regulatory networks. GenoTech allows the user to specify a GRN on Graphical User Interface (GUI) according to the asynchronous multivalued logical functions of René Thomas, and to simulate and/or analyse its qualitative dynamical behaviour. René Thomas discrete modelling of gene regulatory network (GRN) is a well known approach to study the dynamics of genes. It deals with some parameters which reflect the possible targets of trajectories. Those parameters are priory unknown. These unknown parameters are fetched using another model checking tool SMBioNet. SMBioNet produces all the possible parameters satisfying the given Computational Logic Tree (CTL) formula as input. This approach involving logical parameters and conditions also known as qualitative modelling of GRN. However, this approach neglects the time delays for a gene to pass from one level of expression to another one i.e. inhibition to activation and vice versa. To find out these time delays, another modelling tool HyTech is used to perform hybrid modelling of GRN. We have developed a Java based tool called GenNet http://asanian.com/gennet to facilitate the model checking user by providing a unique GUI layout for both qualitative and quantitative modelling of GRNs. As we discussed, three separate modelling tools are used for complete modelling and analysis of a GRN. This process is much lengthy and takes too much time. GenNet assists the modelling users by providing some extra features i.e. CTL editor, parameters filtering and input/output files management. GenNet takes a GRN network as input and does all the rest of computations i.e. CTL verification, K-parameters generation, parameter implication to GRN, state graph, hybrid modelling and parameter filtration automatically. GenNet serves the user by computing the results within seconds that were taking hours and days of manual computation

El barómetro es un instrumento de medición atmosérica, específicamente utilizado en la determinación de la fuerza por unidad de superficie ejercida por el peso de la atmósfera. Existe un gran número de equipos atmoféricos con distintos tipos de estos aparátos y son diariamente utilizados ya que la presión atmosférica juega un papel importante en la determinación y pronóstico del tiempo así como en el área de investigación al momento de realizarse experimentos ya que pueden llegar a afectar o hacer variar el funcionamiento de muchos aparatos electrónicos y mecánicos.

This research paper aims at exploiting efficient ways of implementing the N-Body problem. The N-Body problem, in the field of physics, predicts the movements and planets and their gravitational interactions. In this paper, the efficient execution of heavy computational work through usage of different cores in CPU and GPU is looked into; achieved by integrating the OpenMP parallelization API and the Nvidia CUDA into the code. The paper also aims at performance analysis of various algorithms used to solve the same problem. This research not only aids as an alternative to complex simulations but also for bigger data that requires work distribution and computationally expensive procedures.

Este artigo tem como objetivo relatar e detalhar a construção de um conversor buck-boost. Cuja a função deste é converter uma tensão cc (corrente contínua) de entrada, em outra tensão cc em sua saída, de valor mais elevado ou inferior dependendo de sua configuração. Destaca-se aqui o uso de um semi condutor MOSFET que funciona como uma chave controladora. Na elabiração deste está destacada o funcionamento, principais características e toda a parte de simulação e comprovação prática deste conversor.
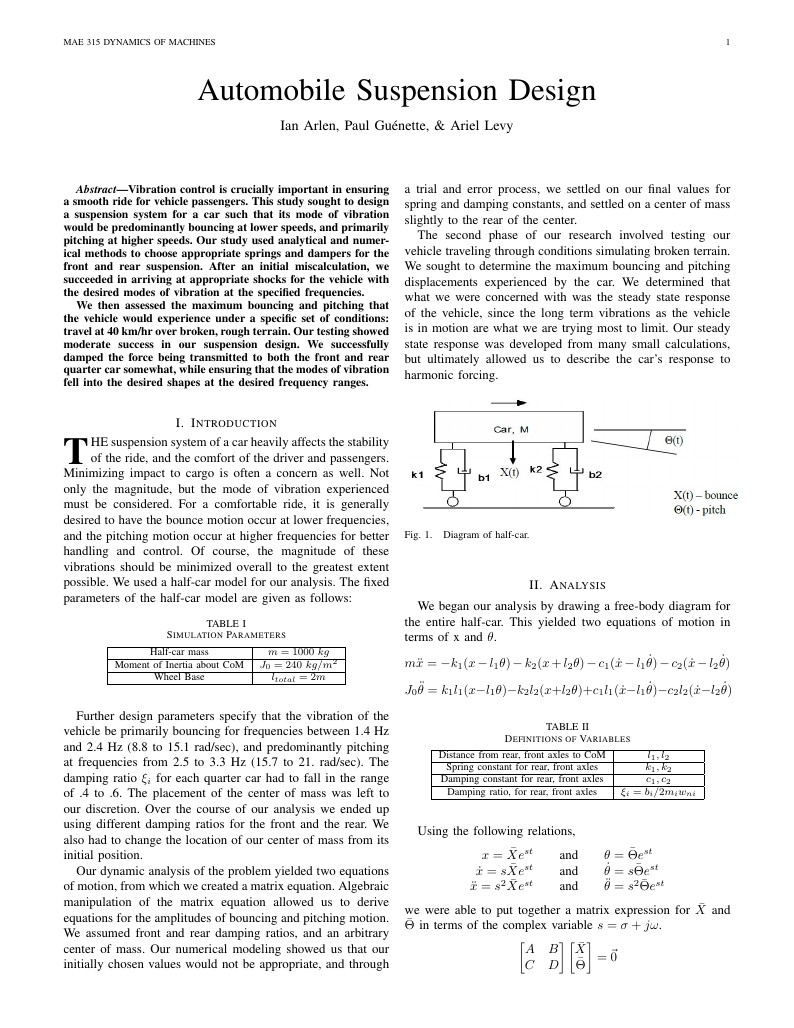
Vibration control is crucially important in ensuring a smooth ride for vehicle passengers. This study sought to design a suspension system for a car such that its mode of vibration would be predominantly bouncing at lower speeds, and primarily pitching at higher speeds. Our study used analytical and numerical methods to choose appropriate springs and dampers for the front and rear suspension. After an initial miscalculation, we succeeded in arriving at appropriate shocks for the vehicle with the desired modes of vibration at the specified frequencies. We then assessed the maximum bouncing and pitching that the vehicle would experience under a specific set of conditions: travel at 40 km/hr over broken, rough terrain. Our testing showed moderate success in our suspension design. We successfully damped the force being transmitted to both the front and rear quarter car somewhat, while ensuring that the modes of vibration fell into the desired shapes at the desired frequency ranges.

In this project the behavior of the Faraday cage as an insulator against an induced load, either by an effect of nature as lightning or lightning or power surges be considered. As we know the Faraday cage is a conductor of electric current and therefore theoretically there will be inside a magnetic field or electromagnetic wave in the same way there will be no magnetic field.

Cour 1 ere AS
\begin
Discover why over 25 million people worldwide trust Overleaf with their work.